
Genetec recognizes Data Privacy Day by sharing physical security best practices
by CM staff
Companies that haven’t taken appropriate steps to protect data are facing tens of millions of dollars in fines for violations.
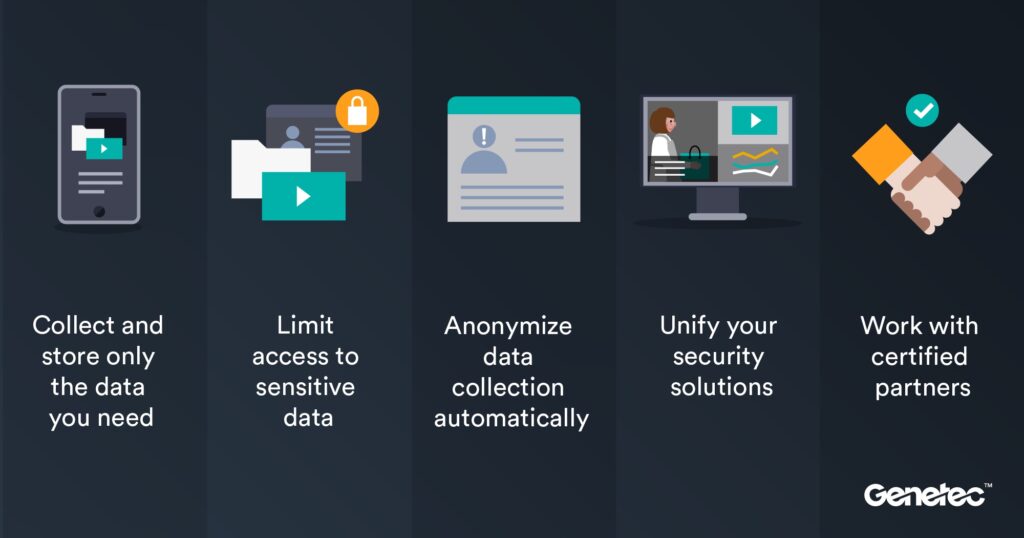
Photo: Genetec.
MONTRÉAL — In recognition of international Data Privacy Day, Genetec Inc., a technology provider of unified security, public safety, operations, and business intelligence solutions, shared data protection best practices to help physical security leaders protect privacy, safeguard data, and enable trust without compromising security.
Currently, 71 per cent of countries have initiated data privacy legislation, and companies that haven’t taken appropriate steps to protect data are facing tens of millions of dollars in fines for violations. In the physical security industry, acquiring digital information such as surveillance footage, photos, and license plate information is necessary to help protect people and assets and provide a valuable source of actionable business intelligence.
“Security and privacy are not mutually exclusive,” said Christian Morin, Chief Security Officer at Genetec. “By following best practices and ensuring privacy is designed into their physical security solutions, organizations can have the highest levels of security while respecting personal privacy and complying to privacy laws.”
Best practices for ensuring video surveillance, access control and automatic license plate recognition systems meet data privacy standards include:
Collect and store only the data the organization truly needs. Reduce your exposure to risk in the event of a data breach with simple steps. Consider adjusting a camera’s field of view so it doesn’t record areas that do not require monitoring. Set protocols to automatically archive or delete physical security data based on relevance. And carefully control what data, how much and for how long it can be shared with other organizations.
Limit access to sensitive data. Grant access to data only to those who need it to do their jobs and monitor those activities to ensure identifying information, like images and access events, is used only as intended. Review access rights regularly so privileges align with user requirements. Using an identity provider, like Microsoft Active Directory, can also help eliminate human error by automating the processes of adding/removing security user accounts, granting rights, or removing users who have left the organization.
Anonymize data collection automatically. New technologies can automatically restrict and protect access to personal data. Consider deploying privacy masking like Genetec KiwiVision™ Privacy Protector that automatically anonymizes images of people, so you can continue to survey surveillance footage while respecting privacy. This technology also offers an additional layer of security that ensures only authorized users can “unlock” and view unmasked footage while maintaining an audit trail.
Unify your security solutions. When video surveillance, access control, evidence management, and other sensors operate under one platform, it becomes much easier to access and manage all your data and create reports for a variety of systems and sensors from a single interface. A unified system simplifies the process of tracking system and device health and streamlines software and firmware updates which is key to mitigating the threat of data breaches.
Work with certified partners. Make sure your system providers are properly certified (ISO 27001, 27017 standards, UL 2900-2-3 level 3 cybersecurity certification, and SOC2 compliance), and that they develop all their technology based on principles of privacy. A cyber resilient physical security system will contribute to keeping the data collected from IoT devices and sensors across the physical security network private.