
A shield against the darkness: keeping Canadian business safe from cyberattacks
by Will Mazgay, Digital Editor, Canadian Manufacturing.com

Keeping a company’s digital assets safe requires the right tools, smart investment and a proactive, transparent attitude towards security

As the sophistication of cyber threats increases daily, Canadian businesses often find they are playing catch-up when it comes to protecting digital assets. PHOTO: Pixabay
TORONTO—Canadian businesses are nervous, and they should be. Cyberattacks are on the rise, and the threats are becoming more sophisticated every day. Intellectual property, the personal information of clients and employees, and in the case of manufacturers, operating systems, are all vulnerable. So the question is: how do businesses protect themselves?
Companies need to fight fire with fire. The security platforms businesses rely on, the practices they employ, and even their corporate philosophies need to be as adaptable as the dangers they are combatting.
To create an effective cybersecurity strategy, there are a few things businesses need to keep in mind.
Abhay Raman is a cybersecurity leader at Ernst & Young (EY). He and his team handle organizational protection, incident response and forensic investigations in the event of a breach.
Raman identifies four things that every company must accomplish to protect its assets:
- Sensing attackers: You need to be able to spot breaks in patterns and abnormalities in your system.
- Resisting attacks: Have mechanisms in place to make it as hard as possible for intruders to get into your system.
- Reacting to breaches: If you are compromised, how quickly can you contain the damage without disrupting business? It is also important to keep evidence of a breach intact, for both private forensic investigators and the government bodies you will need to notify.
- Managing identities and access: Ensuring the wrong people aren’t accessing your network is crucial. This means cutting off former employees’ access. Protecting personal accounts should also be a priority; take the time to educate employees on password and signature safety.
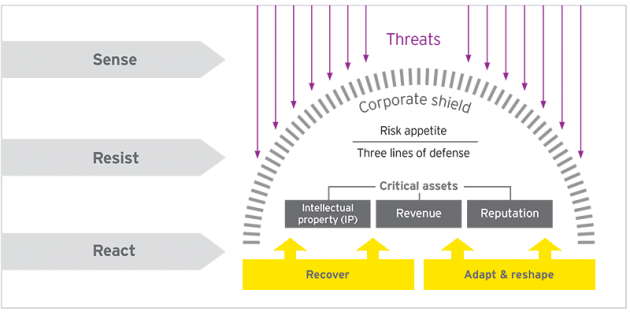
EY’s cybersecurity team preaches a multi-faceted approach to protect digital systems: sense, resist and react to breaches. PHOTO: EY
Tools of the Trade
Accomplishing the aforementioned tasks requires an effective cybersecurity platform.
David Masson, Canadian country manager of cybersecurity firm Darktrace, preaches the importance of a security system that can learn and adapt to ever-evolving threats. He believes that artificial intelligence is the future of cybersecurity.
Darktrace’s self-learning program builds an immune system for digital networks. Network traffic is picked up, compartmentalized and analysed. From this analysis, mathematical models for everything in a specific network are created. Based on these models, the program learns the normal pattern of life and behaviour in that network. It can then identify deviations in the pattern of life and spot the anomalies that signal the beginning of an attack.
This AI-based program is continuously reassessing and relearning the pattern of life as changes develop.
“It’s just like the human immune system. You don’t have to tell the immune system what to do, it just knows that something is amiss right away, and that’s what we’ve managed to mimic,” Masson said.
Masson argues that this continuously evolving approach to security is the only way to keep up with the sophistication of digital threats, and that human minds are not fast enough to accomplish this.
Yuri Frayman, CEO of cybersecurity specialist Zenedge, agrees with Masson’s assessment.

Zenedge’s self-learning platform offers protection from malicious bots. PHOTO: Zenedge
Frayman says old security approaches based on the signature and identity of users trying to infiltrate a system are obsolete, because hackers switch devices and Internet Protocol addresses regularly.
“Signature-based mitigation, what the world is using today for the most part, is being outdone. Once the IP address has been exposed, the hacker won’t use it again. When you block an IP, you can be blocking an actual customer instead of a hacker. That’s the number one challenge,” said Frayman.
This is a challenge Frayman attempts to tackle with Zenedge’s security platform, which, much like Darktrace’s system, relies on AI and machine learning technology.
“Once you tell a machine that this is the typical type of hacker, this is the typical type of activity of a hacker, a machine now understands how the hacker behaves,” said Frayman.
Frayman’s team is continuously feeding their platform new information, to help it to learn, adapt and strengthen digital defences.
Zenedge releases at least one patch update a month, which can be administered quickly because the platform is purely cloud and web based.
“Your defences get upgraded globally when identifying a new threat. If we pick up an attack in Singapore, all of our nodes around the world are updated with new algorithms,” said Frayman.
Web-based systems do not rely on slow-to-update hardware or traditional firewalls.
Traditional firewalls are particularly problematic, as they can take up to 25 days to learn new network behaviour. A web-based firewall can retune a system to new applications or traffic patterns in six hours.
Speed is the name of the game.
Understanding the Threat
Cybersecurity tools, like those offered by Zenedge and Darktrace, are evolving at a breakneck pace, but they have to.
“Imagine for every single report your reading about a breach, that occurs 10-16 times a day, imagine them not being reported. Imagine how many companies are being penetrated that don’t even know,” said Frayman.
Learning how to recognize threats is just as important as having the tools to combat them.
Raman says that even with the most advanced security platform in place, if employees aren’t properly trained to recognize and avoid threats, businesses’ digital systems are at serious risk.
Employee training can help prevent dangers like phishing attacks, which accounted for 51 per cent of cybersecurity threats recognized in EY’s 2016 cybersecurity report.
Malicious emails masquerading as legitimate correspondence used to be easy to spot—they were often riddled with typos and suspicious language—but hackers have upped their game in recent years, and now these messages appear professional and polished.
Phishing emails are often possible because of malware infections, viruses that spy on employees and gradually learn how they communicate with each other. Once the virus has obtained enough information, the hackers send out an email that mimics the writing style of an employee that the attack’s target has regular correspondence with, enticing the target to click on a link or follow a set of instructions.
In the same EY study, malware attacks saw a 10 per cent uptick between 2013 and 2016.
Frayman says that the worst thing businesses can do is not take these threats seriously. He regularly meets executives who believe that the strength of their network alone can protect them from hackers, as well as business leaders who don’t understand how easy it is for employees to open the gates for the wolves.
“I can’t even begin to tell you, there’s still companies that think ‘we have nothing to fear,’” he said.
Increasingly powerful and intelligent technology is vitally important to keeping digital systems safe, but the human component is all too often lost in this equation. People make mistakes that leave them susceptible to theft and fraud in the real world all the time, and the way they behave online is no different. Education is a powerful weapon for keeping networks safe.
IoT Threats
Protecting IoT systems means controlling access to data, keeping devices bug free and patching vulnerabilities into systems quickly. PHOTO: Pixabay
Whether it’s through applying smart security tools or training employees to recognize threats, securing information technology systems is a difficult task. But securing Internet of Things networks brings with it an entirely unique and arduous set of challenges.
When you have hundreds of devices communicating across an IoT network, the amount of data traffic is immense. Companies need to be wary of suspicious traffic, keep devices bug free and patch vulnerabilities into systems quickly.
However, one of the biggest challenges when it comes to IoT protection is securing various methods of accessing data.
“If there’s 5,000 ways to access data, you have to protect those 5,000 ways,” said Raman.
If this sounds labour intensive and costly, it is, but not investing in IoT protection can be a perilous mistake. This is particularly important for the manufacturing sector, where the stakes are incredibly high.
Wireless connections between machines form the basis of modern operating networks, and all it takes is one little bug to bring an entire system of state-of-the-art industrial machinery grinding to a halt.
A hacker shutting down an operating system can disrupt a company’s entire production and supply chain cycle, costing millions, but Masson points to a more insidious form of sabotage, what he calls “trust attacks”.
Trust attacks don’t shut down operating systems, but instead alter manufacturing processes in subtle ways, compromising the quality of the product and eroding trust in the company.
Masson provided the example of a water treatment plant’s incident command system being infiltrated, changing the purification levels in the water. In this case, the company’s reputation and the safety if its customers were at stake.
When it comes to trust attacks, Masson says, “You just don’t know. You don’t have that visibility in the network; you never saw that subtle change. The only way you find out about it is once the problem comes up.”

Wireless connections between machines form the basis of modern operating networks, and all it takes is one little bug to bring an entire system of state-of-the-art industrial machinery grinding to a halt. PHOTO: Mixabest via Wikimedia Commons
The best way to prevent against industrial sabotage is to ensure that attackers can’t get into IoT networks in the first place. Respect for the threat that lurks in the shadows of the digital world and an appreciation for what is at stake can go a long way towards keeping a company safe.
While there is still a lot of ignorance and hubris when it comes to cybersecurity, Raman believes Canadian businesses are starting to take these threats seriously.
He says most companies in this country are spending money in the right places, on security training, event monitoring, security testing, identity protection and data leakage prevention, and they are spending more of it. Indeed, 53 per cent of respondents in EY’s security survey said their cybersecurity budgets had increased over the last year.
While Raman says this is good news, he believes there is still a lot of work needed to bring corporate cybersecurity to where it should be in Canada.
Ultimately, cybersecurity starts and ends with the senior leadership of an organization. Security leadership doesn’t just mean investing the appropriate amount of capital in the right places, it means creating a company-wide culture of vigilance and accountability. Executives must not only encourage employees to avoid threats but to report them to security teams, and create an environment where employees feel safe disclosing weaknesses in security systems.
Cybersecurity only works when it is approached collaboratively. After all, when it comes to the safety of corporate information and operating systems, everyone’s livelihood is at stake.