
The next big attack: WannaCry could be just the beginning
by Will Mazgay, Digital Editor

While the business world is still recovering from the global ransomware attack that crippled the digital landscape, one cybersecurity expert predicts future attacks are on the way, and soon
Ransomware locks users out of their personal or organizational information and demands a ransom to get it back. PHOTO: Christiaan Colen via Flickr
TORONTO—As companies and individuals around the world are still trying to kill the WannaCry ransomware virus, clean up their systems and recover their data, one cybersecurity expert is already looking out for the next big catastrophe.
Yuri Frayman, CEO of the cybersecurity firm Zenedge, believes the May 12 infection is just the latest in a string of future attacks, and that the hackers behind WannaCry will build on the damage done and weaknesses exploited by their handiwork to create a more resilient and potent virus.
“I can tell you they are already working on the next WannaCry. You’ll see WannaCry 2, 3 and 10. These hackers are continuously innovating,” Frayman said.
We may be two weeks removed from the launch of global cyber assault that crippled government infrastructure, businesses and home computers around the world, but the attackers are still raking in profits.
As of May 29, deposits are still being made into the Bitcoin accounts associated with the WannaCry attack, according to Elliptic, a Bitcoin watchdog that is tracking the ransom payments.
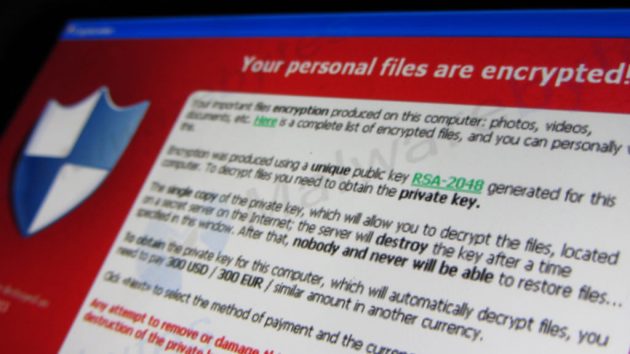
The WannaCry virus is named for the WannaCrypt technology used to execute it, and it encrypts personal or organizational information, blocking access to it. A ransom is demanded by the hackers responsible to get control of the information back.
WannaCry has been labeled the biggest attack of its kind in history, but it could be just the beginning of a series of devastating cybercrimes.
A Pervasive Contagion
The idea that there will be future versions of this virus is far from broad speculation. There were already attacks using the same ransomware carried out against specific targets back in March and April, though without much fanfare.
This most recent WannaCry was so effective and spread so quickly because of a leaked exploit of Windows operating systems, EternalBlue, created by the U.S.’s National Security Agency.
Frayman says this exploit is incredibly sophisticated, and it managed to spread WannaCry ransomware quickly because of the vast and complex supply chains of the companies affected.
The attack, which hit victims in 150 countries, targeted massive companies like FedEx, pulverized the U.K.’s national health care network, and crippled infrastructure and transportation worldwide.
One estimate released shortly after the attack by cyber risk modeling firm Cyence, reported by CBS News, predicted the global cost could be as high as US$4 billion.
In many cases, the damage has already been done and the recovery effort has been under way since the attack first struck. But this is far from over.
The approximately 300,000 computers that have reportedly been infected are just the cases we know about.
Frayman asserts that there are possibly an equal number of users and businesses who have no idea they are infected, and that in many computers and networks the virus is lying dormant, collecting information and waiting to exploit a weakness and take hold.
“This is about planting a seed that they will be able to materialize six months from now,” Frayman said.
To avoid these seeds sprouting into nasty weeds that can encrypt data and paralyze operations, Frayman recommends approaching cybersecurity professionals to perform a forensic evaluation. Once a detailed scan has determined that a system is infected, an antidote can be administered to kill the virus.
Frayman says his firm has been successful at killing the bug at its source, but he is worried about tertiary links in the affected organizations’ supply chains. Following the virus down these supply chains is proving to be a challenge for cybersecurity professionals because, in Frayman’s estimation, not enough companies are doing their due diligence to ensure that they aren’t infected.
Microsoft released a patch for the vulnerabilities in its operating systems—those users who installed that patch before the May 12 attack began should be safe, but those who haven’t done so are vulnerable.
Regularly patching corporate computers and devices should be standard practice, but home computers are another matter entirely.
It’s easy to forget to install the latest update on a home PC, and often times these important bundles of software can sit idle as unanswered reminders for months. But for those who access corporate networks from home, not keeping up with software patches can cause a contagion to spread from the house to the office in a hurry.
Given how many people around the world work from home, the risk of WannaCry and similar viruses infecting corporate networks through home computers is enormous. This is something companies that think they have made it through this attack unscathed need to consider.
Muddled Motives
Despite the catastrophic damage this attack has caused and the potential for it to have ripple effects throughout the digital world for months to come, much has been made about the missteps of the hackers responsible.
Killswitches embedded in the code of certain iterations of the ransomware, which have slowed its spread, and a poorly planned system of receiving ransom payments have puzzled security experts to this point.
The virus has also made very little money for its attackers, roughly $100,000 to date. This is dramatically disproportionate to its scope or the damage it caused, and a paltry sum compared to other ransomware attacks: A bug called Angler was estimated to pull in $60 million a year before it was shut down.
The lack of monetary success and the perceived blunders of the attackers have prompted some experts to decry this virus as the work of sloppy amateurs using distribution methods beyond their capabilities, and others to suggest that it was politically motivated and designed simply to cause mayhem.
Frayman disagrees, saying that the pervasive nature of the ransomware and its potential to snowball into more devastating and resilient attacks shows an impressive level of sophistication.
“Somebody knew what they were doing,” he said.
He also argues that the attackers’ motivations were not political, but financial.
“This is an industry that is generating a billion dollars a year. This is companies and criminal organizations with the sole purpose of generating revenue and stealing information for future reselling. The bottom line is, it’s a business.”
A recent report by software firm Symantec suggested links between WannaCry and a North Korean linked hacker group, but in the same report Symantec’s researchers noted that the attack doesn’t have the hallmarks of a state-sponsored campaign, but instead that of cybercrime.
Frayman believes the attackers’ financial motivations stretch beyond the small sum of money ransomed by Bitcoin accounts associated with the ransomware.
“I think that there is a greater motive on behalf of the hackers to do other damage. I think this was a smokescreen,” he said.
What that other damage is and what sort of financial windfall the attackers expect to gain from it remains to be seen.
However, given the potential of this virus to spread to new networks, learn vulnerabilities in security systems and adapt to tools designed to kill it, the digital world could be in store for incalculable catastrophe in the future.
Staying Ahead
While the motivations of hackers are crucially important to the cybersecurity analysts and technicians fighting these viruses on the frontlines, for business owners and end users, all that matters is keeping networks safe.
To this end, Frayman recommends employee training to recognize suspicious emails and avoid them. The most common deployment method of ransomware is through phishing emails, nasty Trojan Horses disguised as legitimate corporate correspondence. Not clicking links or opening these emails can help eliminate a lot of problems.
Beyond employee vigilance, security software and firewall technologies are prudent investments for any firm with information that needs to be protected.
After all, once information is encrypted by a hacker there is no guarantee a ransom payment will get it back.
Frayman says CEOs have a responsibility to allocate budgetary resources to cybersecurity, not only to protect their own assets and employees, but their clients as well.
The rapid spread of the next global cyber-attack could be stymied by a stronger commitment, on the part of business leaders, to protecting both individual assets and the corporate ecosystem as a whole.
Frayman believes the next big attack is coming soon, and it is going to cause damage. However, there are lessons to be learned from WannaCry which, if put into practice, could lessen the impact of the next hammer blow.
Whether or not the corporate world will stand up and take notice is yet to be determined.