
Design Engineering: How to mitigate three common industrial network vulnerabilities
by Felipe Sabino Costa

Strategies for harding industrial systems to mitigate damage at each stage of an intrusion.
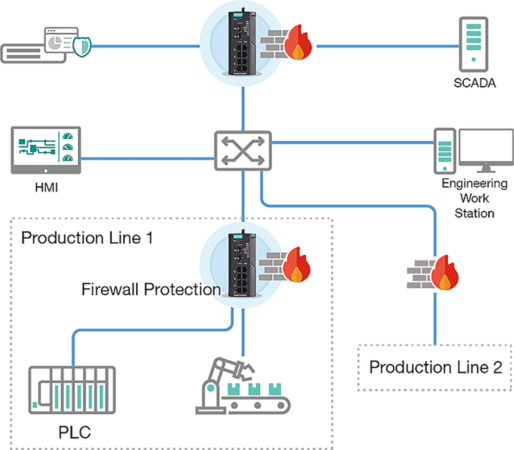
Network segmentation builds boundaries to protect production lines without impacting each other when cybersecurity incidents occur.
Photo: Moxa.
Since industrial networks are primarily built and expanded to address growing business demands, it may be easy for administrators to overlook common system vulnerabilities. For example, when adding a device to a network, do you know which Ethernet switches have unlocked ports or do you simply connect new devices without a second thought?
In today’s world, ignoring common vulnerabilities could put your entire network at risk. The following scenarios summarize common system vulnerabilities that may be exploited during the three main stages of a cyberattack: exploration, utilization and attack.
Stage 1 Vulnerabilities: Exploration and Infiltration Recall the last time you logged onto your network. How complex was your password? Weak passwords may be easier for busy administrators to remember, but they are also easier for malicious actors to crack. Making it easy attackers to guess login credentials is like putting the keys to your house in an obvious location.
This article originally featured in Design Engineering. Read the full version here.